Malaysia’s Cyber Security Laws: A Comprehensive Guide
In this digitalised age, the internet has taken centre stage in our daily lives.
A recent study by Proxyrack revealed that Malaysia ranks third in the world for spending most time online.
While the internet provides us with convenience and enjoyment, it also serves as the seedbed of cyber security issues.
In Q4 2022 (October to December), Malaysia experienced an average of 84 million cyber attacks daily, making Malaysia one of the most vulnerable locations in Asia.
To strengthen national cyber security protection, Malaysia started to work on a comprehensive cyber security law. Dubbed the Cyber Security Bill, the enactment of this new legislation on cyber security is still on its way.
While the bill is yet to be presented in the Malaysian Parliament, various existing laws are also capable of addressing cyber security threats and implementing preventative measures to safeguard against cyber security threats.
Let’s dive in and embark on the exploration of cyber security laws in Malaysia. Off we go!

Computer Crimes Act 1997
As evident from its name, the Computer Crimes Act 1997 (CCA) addresses offences associated with the misuse of computers, including:
- Unauthorised access to computer material
- Unauthorised access with intent to commit or facilitate commission of further offence
- Unauthorised modification of the contents of any computer
- Wrongful communication
Remark: The term “wrongful communication” pertains to the inappropriate sharing of any means of access to a computer to an unauthorised individual.
The regulatory body under CCA is the Royal Malaysian Police (PDRM). Under this legislation, police officers can arrest anyone without a warrant if there is a reasonable belief that individuals have committed or are currently committing a crime under this act.
Any offences related to this act can result in varying penalties, with fines ranging from RM25,000 to RM150,000, imprisonment for 3 to 10 years, or a combination of both.
Notably, the CCA has extraterritorial applicability. This implies that the law applies to individuals of any nationality, both within and outside Malaysia.
If an individual commits a crime under the CCA outside Malaysia, they can face punishment as if the offence occurred within the country.

Source: India Today
Communications and Multimedia Act 1998
The Communications and Multimedia Act 1998 (CMA) serves as the regulatory framework that is aligned with the national policy objectives for the converging communications and multimedia industries in Malaysia.
As outlined in Section 3 of the CMA, the CMA places a premium on information security and network reliability.
Fraudulent or improper use of network facilities, possession of counterfeit access devices, unauthorised access attempts, and interception of communications without lawful authority were prohibited under CMA (Chapter 2, Part X of CMA).
Similar to the Computer Crime Act 1997, the CMA also has extraterritorial applicability.
The Malaysian Communications and Multimedia Commission (MCMC) assumes the role of the regulatory body overseeing the industry.
Since its appointment on the 1st of November 1998, the MCMC has been entrusted with ensuring compliance with the regulatory framework, including licensing conditions, competition practices, technical regulations, and more.

Electronic Commerce Act 2006
As indicated by its name, the Electronic Commerce Act 2006 (ECA) provides legal recognition to electronic messages within commercial transactions. This Act plays a pivotal role in fostering the flourishing growth of digital trade in our country.
While ECA takes centre stage in addressing the legal intricacies of electronic transactions, cyber security issues are intertwined with its effective implementation.
Securing electronic messages, preventing fraud and unauthorised access, and protecting consumer data are critical considerations that align with the goals of ECA to facilitate a secure and legally recognised environment for electronic commerce in our country.
In anticipation of more comprehensive legislative measures, proactive steps are essential for business owners (like you!) in fortifying the systems of businesses against cyber security challenges.
At VeecoTech, we are in arms to consolidate your digital journey with our comprehensive suite of cyber security assessments, including Vulnerability Assessment, Cyber Maturity Pre-Assessment, and Penetration Test.
Feel free to visit this webpage for more details.

Credit: Imgflip
Copyright Act 1987
The Copyright Act 1987 stands as the cornerstone of copyright protection in Malaysia, with a focus on safeguarding various forms of copyrighted works.
This includes literary works such as computer programmes and online materials, along with trade secrets, intellectual property in devices or data, and many more.
The amendment of this Act in 1997 addressed unauthorised transmissions of copyrighted works over the Internet and prohibited the circumvention of technological protection measures that applied to copyrighted works (Section 36A).
Remarkably, offering technology or devices that enable such circumvention is also deemed an offence. These measures aim to ensure robust protection for intellectual property rights, especially for businesses involved in content creation within the ICT and multimedia sectors.
The penalties for non-compliance with the provisions are as follows:
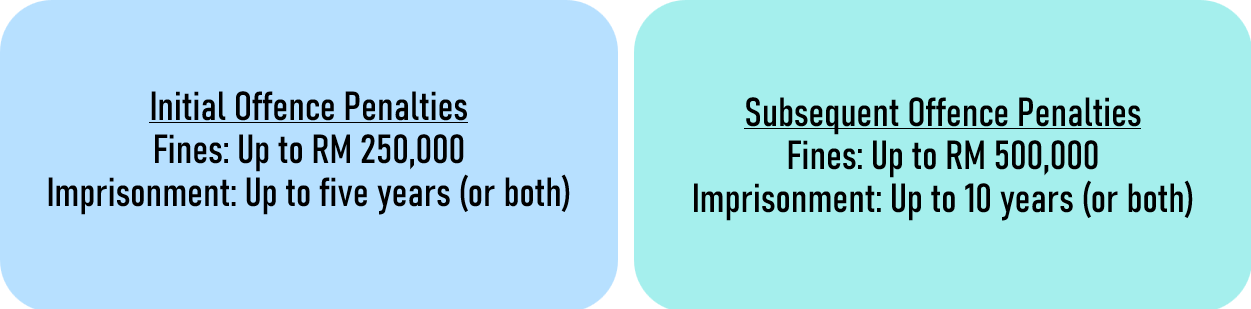
The Copyright Act implies that its jurisdiction is primarily within Malaysia, as there is no mention of its extraterritorial applicability.
Penal Code
The Penal Code is the main statute that codifies most criminal offences and procedures in Malaysia. In cases where cyber-related criminal offences do not specifically fall within the ambit of existing statutes, such offences may be charged under the Penal Code.
One prevalent cyber security issue in Malaysia is phishing.
Whilst there isn’t a specific provision addressing it in the country currently, Section 416 of the Code, which deals with ‘cheat by personation’ can be invoked to counter phishing.
Applying to both real and imaginary personas, this offence targets individuals who pretend to be someone else with the intention to deceive.
Similarly, fraud is a common cyber security concern without a dedicated provision.
However, the Penal Code does cover several criminal offences related to fraud, including theft (Section 378), criminal breach of trust (Section 405), forgery (Section 463), fraudulent deeds (Section 423) and more.
Violation of the provisions under the Penal Code would subject the offender to enforcement by the Royal Malaysian Police. The offender may face penalties involving a fine ranging from RM25,000 to RM150,000 or imprisonment for 3 to 10 years, or both.

Personal Data Protection Act 2010
The Personal Data Protection Act 2010 (PDPA) is the key framework that regulates personal data processing in commercial transactions in Malaysia.
The most relevant PDPA principle in the context of cyber security would be the Security Principle. This principle mandates the implementation of practical measures to protect personal data from loss, misuse, modification, unauthorised access, disclosure, alteration, or destruction.
Non-compliance with the PDPA may result in fines ranging from RM100,000 to RM500,000, imprisonment for one to three years, or both.
Hence, not keeping up with PDPA rules can be a big deal.
Ask yourself:
- Are your systems ready to fend off cyber threats?
- Do your virtual defences align with PDPA guidelines?
If you’re saying “No,” “Not sure,” or “Don’t know,” it might be the perfect time to check out our Cyber Security Assessment Package.
In this package, we’ll dive into vulnerabilities across web apps, mobile apps, systems, and networks, while making sure your business sticks to top-notch industry practices and government standards. Find out more about the assessment package over here!
Conclusion
While these laws can help after a cyber hit, they’re more like cures than shields.
Moreover, the aftermath of a cyber incident is never pretty.
You’ll need to spend money to rebuild your system, waste valuable business operation time while waiting for the system to recover, and risk damage to your business reputation due to perceived vulnerabilities.
Instead of dealing with these consequences, why not consider taking a proactive step by fortifying your systems upfront?
VeecoTech is all set to assist you in strengthening your systems and safeguarding your business from potential cyber threats! Contact us today for expert cyber security solutions.
FAQ
How does the Communications and Multimedia Act 1998 (CMA) play its role in cyber security in Malaysia?
CMA regulates the communications and multimedia industry and places a premium on information security and network reliability.
CMA prohibits:
- Fraudulent or improper use of network facilities
- Possession of counterfeit access devices
- Unauthorised access attempts
- Interception of communications without lawful authority
How does the Copyright Act 1987 contribute to cyber security?
This Act protects intellectual property, including digital content, by prohibiting:
- Unauthorised transmissions of copyrighted works over the Internet
- Circumvention of technological protection measures that applied to copyrighted works
- Offering technology or devices that enable such circumvention
What role does the Electronic Commerce Act 2006 play in shaping the cyber security landscape of Malaysia?
This Act provides a legal framework for electronic transactions, ensuring the security and reliability of online transactions.
What are the penalties for violating the cyber security provisions under these acts and laws in Malaysia?
Penalties for cyber security violations vary, but they may include fines ranging from RM25,000 to RM150,000 or imprisonment for 3 to 10 years, or both.
In cases where cyber offences don’t fall under specific statutes, how are they dealt with under Malaysian law?
Such offences may be charged under the relevant provisions of the Penal Code. This Code ensures that legal measures are in place even when specific statutes are absent.
References:
Acts:
Communications and Multimedia Act 1998
Computer Crimes Act 1997
Copyright Act 1987
Electronic Commerce Act 2006
Personal Data Protection Act 2010
Penal Code
Others:
Basics of Cyber Security Law in Malaysia – Chia, Lee & Associates
Cybersecurity Laws in Malaysia – MahWengKwai & Associates
Malaysia: Cybersecurity – OneTrust Data Guidance
The International Comparative Legal Guide to: Cybersecurity 2019 (2nd Edition)











Leave A Comment